网络防火墙和NAT转发
当一台主机当做网络防火墙的时候,外部的网络报文要经过三条链后才能进入本地网络:PREROUTING,FORWARD,POSTROUTING,但是能起到过滤作用的只能是filter表中的FORWARD链。而且要开启核心转发功能。这样和主机防火墙就没有关系了,INPUT链和OUTPUT链都可以不用管,只设置FORWARD链。
拓扑图:
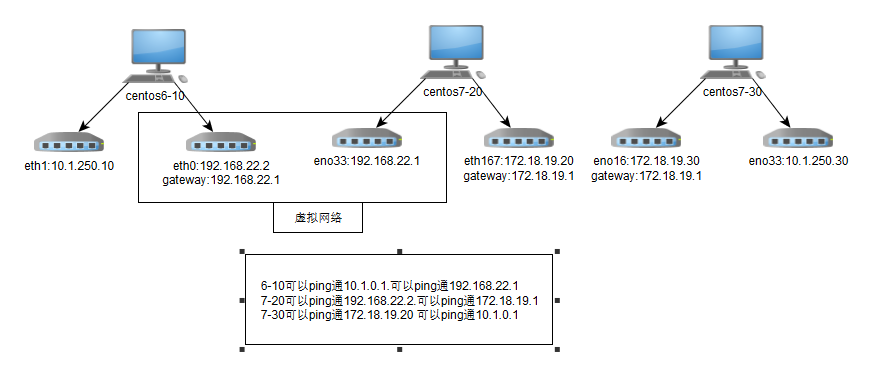
前提:三台虚拟机在一台物理机上面,其中192.168.22.0网络是虚拟网络,不是物理网络,172网段和10网段是物理网络。6-10和7-30连接10网络是为了下载rpm包方便,不参与此处实验。中间7-20主机扮演的是防火墙主机,7-30扮演的是互联网的其他主机,6-10扮演的是局域网内的一个主机。并且如上所说,网络都是互通的。
清空三台虚拟机的防火墙,不然出错。
centos6:#iptables -F, centos7: #systemctl stop firewalld #iptables -F
–
在6-10主机:可以ping通172.18.19.20主机,在7-20没有打开转发的情况下, 因为6-10网关是192.168.22.1,不是本地IP都要转发到网关, 网关发现要ping的172的IP就是本机的IP,直接返回响应。 [root@localhost ~]#ping 172.18.19.20 PING 172.18.19.20 (172.18.19.20) 56(84) bytes of data. bytes from 172.18.19.20: icmp_seq=1 ttl=64 time=0.471 ms 可以用tcpdump命令来抓包测试,当在6-10主机ping 172.18.19.30。用tcpdump在7-20主机抓包eno33网卡,可以发现ping报文,当抓eno16网卡的时候,发现没有报文经过。 在7-20主机: [root@localhost ~]#tcpdump -i eno33554984 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno33554984, link-type EN10MB (Ethernet), capture size 65535 bytes 12:53:13.322056 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 54048, seq 69, length 64 12:53:14.322253 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 54048, seq 70, length 64 [root@localhost ~]#tcpdump -i eno16777736 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 无数据 在7-20主机:打开路由转发功能 [root@localhost ~]#echo 1 > /proc/sys/net/ipv4/ip_forward 在6-10主机: [root@localhost ~]#ping 172.18.19.30 在7-20主机: [root@localhost ~]#tcpdump -i eno33554984 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno33554984, link-type EN10MB (Ethernet), capture size 65535 bytes 13:05:16.180902 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 64288, seq 201, length 64 13:05:17.180306 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 64288, seq 202, length 64 [root@localhost ~]#!tc tcpdump -i eno16777736 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 13:03:17.153331 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 64288, seq 82, length 64 在7-30主机: [root@localhost ~]#tcpdump -i eno16777736 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 13:09:52.242687 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 64288, seq 477, length 64 13:09:52.242932 IP 172.18.19.30 > 192.168.22.2: ICMP echo reply, id 64288, seq 477, length 64 因为ping包不在172同一网段内,7-30主机将ping的返回包发给了172.18.19.1网关了。 这里将172.18.18.30的网关设置为172.18.19.20 在7-30主机: [root@localhost ~]#route del -net 0.0.0.0 gw 172.18.19.1 [root@localhost ~]#route add default gw 172.18.19.20 就可以看到6-10主机有回应了。
在6-10主机安装httpd服务,并打开,可以在7-30主机访问到。
在7-30主机安装httpd服务,并打开,可以在6-10主机访问到。
为FORWARD链增加一条规则来设置默认策略,以防清空列表无法工作
[root@localhost ~]#iptables -A FORWARD -j DROP [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 2 packets, 156 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
此时内外都不能访问网站,都被防火墙drop掉了。
让内网访问互联网的任意web服务。
[root@localhost ~]#iptables -I FORWARD -s 192.168.22.0/24 -p tcp --dport 80 -j ACCEPT [root@localhost ~]#iptables -I FORWARD -d 192.168.22.0/24 -p tcp --sport 80 -j ACCEPT [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 529 ACCEPT tcp -- * * 0.0.0.0/0 192.168.22.0/24 tcp spt:80 833 ACCEPT tcp -- * * 192.168.22.0/24 0.0.0.0/0 tcp dpt:80 1816 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
此时6-10主机可以访问到7-30的web服务。并且FORWARD链上有报文匹配
进一步简化,只要是已建立的报文都是安全的,可以将第一条规则替换掉。
[root@localhost ~]#iptables -D FORWARD 1 [root@localhost ~]#iptables -I FORWARD -m state --state ESTABLISHED -j ACCEPT [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 1 packets, 32 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED 0 ACCEPT tcp -- * * 192.168.22.0/24 0.0.0.0/0 tcp dpt:80 2176 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
此时6-10主机可以访问到7-30的web服务。并且FORWARD链上有报文匹配
可以再次简化,并增加21,22号端口
[root@localhost ~]#iptables -R FORWARD 2 -s 192.168.22.0/24 -p tcp -m multiport --dport 21:23,80 -m state --state NEW -j ACCEPT [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 902 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED 0 ACCEPT tcp -- * * 192.168.22.0/24 0.0.0.0/0 multiport dports 21:23,80 state NEW 2176 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
网页可以访问,ssh可以登录,注意:ssh远程登录上以后和当前的界面一模一样,一直以为没有登录上,可以通过ifconfig看ip地址来查看。坑坑
NAT转发
分类:
源地址转换:SNAT,局域网内的客户端请求互联网的服务器,在最后要离开公网的网卡的时候才转换,放在POSTROUTING链上,就是将所有内网的IP都转换为一个公网IP。
静态地址转换:外网地址是固定的
动态地址转换:外网地址是动态的
可以适用:MASQUERADE:懒,不写了
目标地址转换:DNAT,局域网内有服务器,互联网客户端请求局域网的服务器,是刚进公网网卡的时候就要转换,放在PROROUTING链上,将一个公网IP转换为几个内网IP。
端口转换PAT:port address transfore
当内网中有三台物理服务器,提供web服务,ftp服务,mail服务,但是只有一个公网IP,可以设置一个主机防火墙,当外部客户端请求web服务的时候,会通过nat转换并发送到提供web服务的物理服务器。
—————————————————我是谁———————————————————–
示例:源地址转换
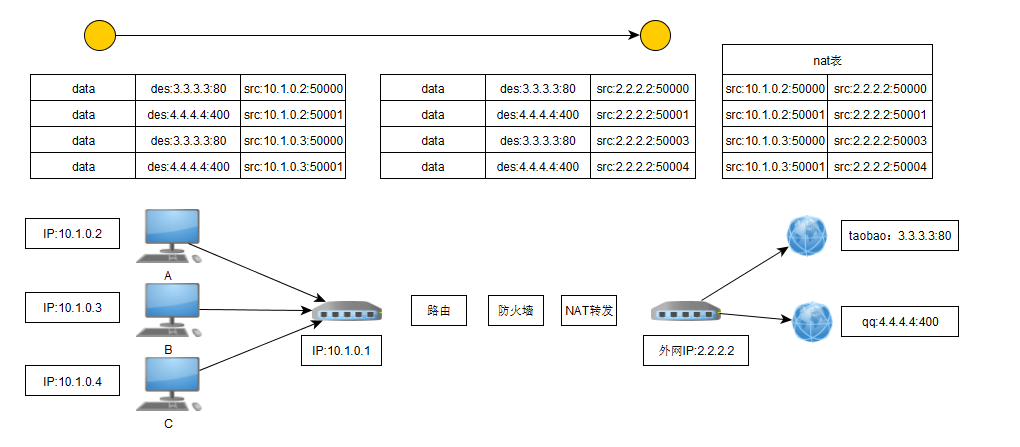
当本地网络中A,B两台电脑同时访问淘宝网页和登录qq的时候,每台电脑都要把请求发送到淘宝服务器,也要把qq的请求发送到qq的服务器。
在局域网中ip报文如上图中的AA所示,报文到达网关(10.1.0.1)的时候,先经过路由,让路由选择该把此报文发送给哪个路由,即下一跳。经过路由的时候报文源IP和目标IP都不会发生变化,还是AA所示的格式。再经过防火墙过滤,快要经过公网网卡的时候,进行nat转换,一个是内网地址必须转换为公网地址才能发送,二是也可以隐藏本局域网内部的网络情况,统一由一个公网IP代理。
在外面看来,所有的服务局域网内的所有服务都是由一个公网IP来进行访问的,
报文返回的时候相反,报文进入外网地址后,先根据保存的nat表进行转换,转换为本地IP和端口,然后发送给各个电脑。
照这样讲,返回报文不用经过路由就可以?
看看路由自带的nat表
————————————-当当当———————————–
还是上面的虚拟机配置,继续做实验,
将7-20防火墙主机防火墙清空,
在6-10主机访问7-30主机的httpd服务,可以在7-30主机httpd日志里查到是:192.168.22.2 地址访问的,这个是防火墙的内网地址,如何将其内网地址隐藏,用nat转发
在iptables的扩展命令里面,属于可执行的动作
SNAT:This target is only valid in the nat table, in the POSTROUTING and INPUT chains, and user-defined chains which are only called from those chains.
–to-source [ipaddr[-ipaddr]]
未设置之前:
主机:6-10:发送ping请求 [root@localhost ~]#ping 172.18.19.30 PING 172.18.19.30 (172.18.19.30) 56(84) bytes of data. bytes from 172.18.19.30: icmp_seq=1 ttl=63 time=0.578 ms 主机7-20 [root@localhost ~]#tcpdump -i eno33554984 -nn icmp #防火墙内网网卡 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno33554984, link-type EN10MB (Ethernet), capture size 65535 bytes 19:12:33.521397 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 63507, seq 53, length 64 19:12:33.522075 IP 172.18.19.30 > 192.168.22.2: ICMP echo reply, id 63507, seq 53, length 64 [root@localhost ~]#tcpdump -i eno16777736 -nn icmp #防火墙公网网卡 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 19:12:16.493475 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 63507, seq 36, length 64 19:12:16.493965 IP 172.18.19.30 > 192.168.22.2: ICMP echo reply, id 63507, seq 36, length 64 主机7-30 [root@localhost ~]#tcpdump -i eno16777736 -nn icmp #服务器数据包 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 19:12:42.534878 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 63507, seq 62, length 64 19:12:42.534984 IP 172.18.19.30 > 192.168.22.2: ICMP echo reply, id 63507, seq 62, length 64
设置nat转换之后:
在7-20主机: [root@localhost ~]#iptables -t nat -A POSTROUTING -s 192.168.22.0/24 -j SNAT --to-source 172.18.19.20 [root@localhost ~]#iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 SNAT all -- * * 192.168.22.0/24 0.0.0.0/0 to:172.18.19.20
–
主机:6-10:发送ping请求 [root@localhost ~]#ping 172.18.19.30 PING 172.18.19.30 (172.18.19.30) 56(84) bytes of data. bytes from 172.18.19.30: icmp_seq=1 ttl=63 time=0.578 ms 主机7-20 [root@localhost ~]#!t tcpdump -i eno33554984 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno33554984, link-type EN10MB (Ethernet), capture size 65535 bytes 20:09:38.595011 IP 192.168.22.2 > 172.18.19.30: ICMP echo request, id 56352, seq 7, length 64 20:09:38.595442 IP 172.18.19.30 > 192.168.22.2: ICMP echo reply, id 56352, seq 7, length 64 [root@localhost ~]#tcpdump -i eno16777736 -nn icmp #防火墙公网网卡 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 20:09:52.618004 IP 172.18.19.20 > 172.18.19.30: ICMP echo request, id 56352, seq 21, length 64 20:09:52.618570 IP 172.18.19.30 > 172.18.19.20: ICMP echo reply, id 56352, seq 21, length 64 主机7-30 [root@localhost ~]#tcpdump -i eno16777736 -nn icmp #服务器数据包 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eno16777736, link-type EN10MB (Ethernet), capture size 65535 bytes 20:09:59.628846 IP 172.18.19.20 > 172.18.19.30: ICMP echo request, id 56352, seq 28, length 64 20:09:59.628893 IP 172.18.19.30 > 172.18.19.20: ICMP echo reply, id 56352, seq 28, length 64
可以发现内网的报文经过防火墙的时候会进行nat转换,经过防火墙的公网地址的时候,报文已经发生改变了。返回的时候也是。
——————————–啦啦啦————————————————
DNAT
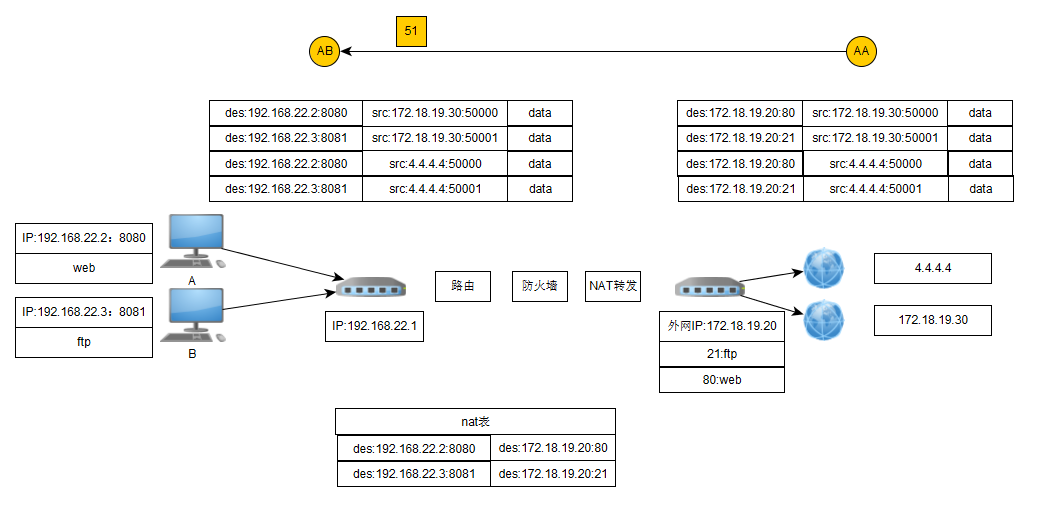
作用,当路由的外面连接的是公网地址的时候,可以自己在内网做个网页,通过dnat转换,通过外网来访问内网的网站。
下面的实验的拓扑图如上,互联网所有的访问,在防火墙都会经过nat转换,转换为局域网内对应主机和对应的端口,内网的web服务不一定要监听在80端口,只要对应的服务套接字不同就可以正常工作。
DNAT:This target is only valid in the nat table, in the PREROUTING and OUT‐PUT chains, and user-defined chains which are only called from those chains.
–to-destination [ipaddr][:port] #不加要转换的端口表示对应的端口不变。
在6-10主机上添加一个IP地址来模拟另一台主机,并配置好httpd对应的端口8080,这里的端口是随意设置的。
[root@localhost ~]#ifconfig eth0:0 192.168.22.3/24 up [root@localhost /etc/httpd/conf]#vim httpd.conf Listen 8080 [root@localhost /etc/httpd/conf]#service httpd restart [root@localhost /etc/httpd/conf]#ss -tnl #保证对应的端口是监听的 LISTEN 0 128 :::8080
在7-20主机上,同时清除snat转换,设置nat转换,所有访问172.18.19.20的80端口的报文,都经过nat转换发送给192.168.22.2的8080端口
[root@localhost ~]#iptables -t nat -F [root@localhost ~]#iptables -t nat -A PREROUTING -d 172.18.19.20 -p tcp --dport 80 -j DNAT --to-destination 192.168.22.2:8080 [root@localhost ~]#iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:80 to:192.168.22.2:8080 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
在7-30主机,访问的是防火墙的80端口,但是实际是局域网内的8080端口。工作正常。7-20主机没有安装httpd服务。
[root@localhost ~]#curl 172.18.19.20 192.168.22.2
测试ssh,
在7-20主机:假如在防火墙主机加一条,凡是访问防火墙22号端口都转发到内网中的(192.168.22.3)主机,
[root@localhost ~]#iptables -t nat -A PREROUTING -d 172.18.19.20 -p tcp --dport 22 -j DNAT --to-destination 192.168.22.3:22 [root@localhost ~]#iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 60 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:80 to:192.168.22.2:8080 0 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:22 to:192.168.22.3:22 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
这样在7-30主机登录(172.18.19.20)的ssh服务的时候,实际是访问的内网(192.168.22.3)主机的ssh服务。登录后看本机的ip地址是内网的。
因为DNAT转换是数据报文刚进入防火墙主机的外网网卡后,就会进行NAT转换,将本机的ssh报文中的IP转换为内网的IP,因此访问的是内网的ssh。
为了ssh的安全,一般将内网的ssh服务隐藏起来,防火墙nat上设置高位端口映射, 即设置nat转换:访问(172.18.19.20:22022)则转到内网某个主机的ssh。
[root@localhost ~]#iptables -t nat -R PREROUTING 2 -d 172.18.19.20 -p tcp --dport 22022 -j DNAT --to-destination 192.168.22.3:22 [root@localhost ~]#iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 60 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:80 to:192.168.22.2:8080 0 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:22022 to:192.168.22.3:22 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
这样的话
[root@localhost ~]#ssh 172.18.19.20 #访问的是防火墙的ssh
[root@localhost ~]#ssh -p 22022 172.18.19.20 #访问的是内网指定主机的ssh
——————————————–呵呵呵—————————————————–
重定向:表示访问本机的一个端口的时候,会自动重定向到本机的另外一个端口,比如本机的httpd服务为8080端口,将此端口重定向为80端口,则远端的主机也可以正常访问httpd服务。
REDIRECT:This target is only valid in the nat table, in the PREROUTING and OUT‐ PUT chains, and user-defined chains which are only called from those chains.
–to-ports port[-port]
还是接着上面的操作,将防火墙的80NAT的转换清除,
在7-20主机 [root@localhost ~]#iptables -t nat -R PREROUTING 1 -d 172.18.19.20 -p tcp --dport 80 -j DNAT --to-destination 192.168.22.3 [root@localhost ~]#iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:80 to:192.168.22.3 60 DNAT tcp -- * * 0.0.0.0/0 172.18.19.20 tcp dpt:22022 to:192.168.22.3:22 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
因为(192.168.22.3)的httpd服务已经是8080端口了,只要重定向就可以
在6-10主机 [root@localhost ~]#iptables -t nat -A PREROUTING -d 192.168.22.3 -p tcp --dport 80 -j REDIRECT --to-ports 8080 [root@localhost ~]#iptables -t nat -nvL Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 REDIRECT tcp -- * * 0.0.0.0/0 192.168.22.3 tcp dpt:80 redir ports 8080 Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination
可以通过7-30主机访问到httpd服务
[root@localhost ~]#curl 172.18.19.20 192.168.22.2
原理:互联网用户访问防火墙的80端口httpd服务,防火墙根据nat转发,将该套接字发送到内网对应主机的80端口上,内网主机也有nat表,将80端口的报文重定向到8080端口,访问在8080端口的httpd服务。
——————————————–呵呵呵—————————————————–
用户自定义链适用
用户自定义链只能被默认的链所调用,不能单独使用,
接着上面的实验,外部网络访问内网的服务器:
先清空防火墙的所有规则,再加一条自己创建的filter链,
[root@localhost ~]#iptables -A FORWARD -m state --state ESTABLISHED -j ACCEPT [root@localhost ~]#iptables -N web_in [root@localhost ~]#iptables -A web_in -d 192.168.22.0/24 -p tcp --dport 80 -j ACCEPT [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain web_in (0 references) pkts bytes target prot opt in out source destination 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.22.0/24 tcp dpt:80
–
[root@localhost ~]#iptables -A FORWARD -m state --state ESTABLISHED -j ACCEPT [root@localhost ~]#iptables -N web_in [root@localhost ~]#iptables -A web_in -d 192.168.22.0/24 -p tcp --dport 80 -j ACCEPT [root@localhost ~]#iptables -A FORWARD -j DROP [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain web_in (0 references) pkts bytes target prot opt in out source destination 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.22.0/24 tcp dpt:80
此时外部网络不能访问httpd服务,因为自定义的链没有被引用。可以将其调用,可以看到自定义的链调用次数1,这样可以将所有根web有关的规则都定义到一条链上,方便管理,
[root@localhost ~]#iptables -I FORWARD 2 -j web_in [root@localhost ~]#iptables -A web_in -j RETURN [root@localhost ~]#iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state ESTABLISHED 1216 web_in all -- * * 0.0.0.0/0 0.0.0.0/0 1216 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain web_in (1 references) pkts bytes target prot opt in out source destination 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.22.0/24 tcp dpt:80 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
RETURN:返回调用的链表,放到自定义链的最后,当自定义链规则匹配完后会自动返回默认的链再开始匹配下面的规则。就像函数调用一样,可以重复嵌套调用。如上面所示,
只有自定义的链为空,并且引用次数为零的时候才能被删除。
文件:
–
–
–
 江哥架构师笔记
江哥架构师笔记
评论前必须登录!
注册